Zero Trust on Mobile Devices
How EMM/MDM fits into modern security architecture
filtruj po kategorii
Filtruj po autorze

How EMM/MDM fits into modern security architecture
Opublikowane przez Tomek Sawko

So Samsung has created an MDM tool that speaks three languages fluently
Opublikowane przez Tomek Sawko

Apple has swept the board! MDM migration, iPhone login, and other new features
Opublikowane przez Tomek Sawko

New tools in the hands of the MDM administrator
Opublikowane przez Tomek Sawko
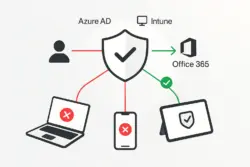
Secure Office 365 by requiring compliant devices!
Opublikowane przez Tomek Sawko

Apple pozamiatało! Migracja MDM, logowanie iPhonem i inne nowości
Opublikowane przez Tomek Sawko

Nowe narzędzia w rękach administratora MDM
Opublikowane przez Tomek Sawko

Czyli Samsung stworzył narzędzie MDM, które mówi płynnie w trzech językach
Opublikowane przez Tomek Sawko

Kompleksowy przewodnik, który zaoszczędzi Ci dziesiątki godzin
Opublikowane przez Tomek Sawko

MDM - o zarządzaniu urządzeniami w organizacji
Opublikowane przez Tomek Sawko

🇵🇱 Przejdź do polskiej wersji tego wpisu / Go to polish version of this post
The traditional approach to IT security, based on the concept of a „trusted” network perimeter (perimeter security), is becoming increasingly less effective in the era of remote work, cloud computing, and ubiquitous mobile devices. In response to these challenges, the Zero Trust architecture was born, which assumes that no user or device should be trusted, regardless of their location (inside or outside the corporate network), and that identity and security status should always be verified before granting access to resources. Mobile devices, often being the weakest link in a security strategy, play a key role in the Zero Trust model, and Enterprise Mobility Management (EMM) / Mobile Device Management (MDM) platforms are an essential tool for its implementation.
The Zero Trust model is based on several fundamental principles:
Mobile devices (smartphones, tablets) represent a huge attack surface:
Therefore, effective management and security of mobile devices is absolutely essential for implementing a credible Zero Trust strategy.
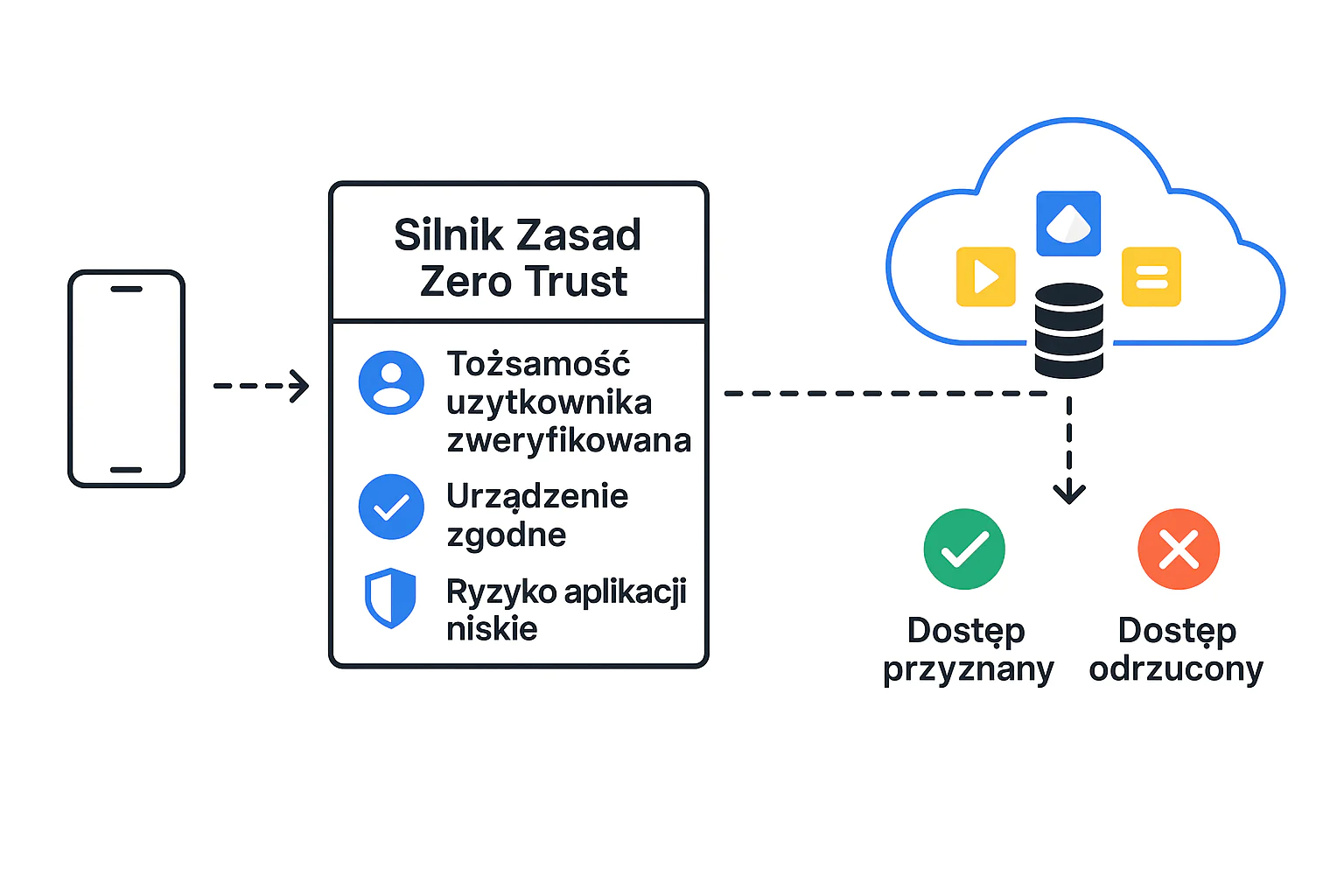
EMM/MDM platforms provide key mechanisms and signals that are fundamental to Zero Trust in the mobile context:
In modern Zero Trust security architecture, mobile devices cannot be treated as trusted simply because they belong to the company or employee. EMM/MDM platforms play an absolutely crucial role, providing mechanisms for device identity verification, security status and compliance assessment, policy enforcement, and data protection in applications. Integration of EMM/MDM with identity management and conditional access systems enables dynamic real-time access decision-making, which is the foundation of an effective Zero Trust strategy for mobile endpoints. Without a solid EMM/MDM solution, implementing Zero Trust in a mobile environment is practically impossible. Modern MDM systems like Proget, Intune, Essentials MDM can largely automate the processes described above.
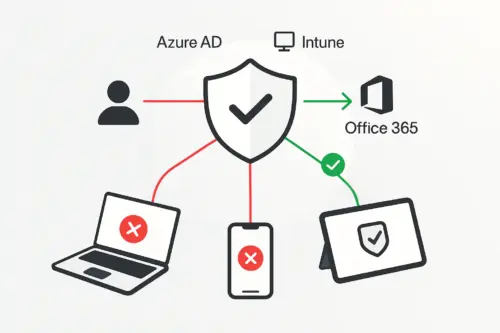
🇵🇱 Przejdź do polskiej wersji tego wpisu / Go to polish version of this post Step by step: Configuring Conditional Access in Azure AD and Compliance Policies in Intune Hi! Today...

🇵🇱 Przejdź do polskiej wersji tego wpisu / Go to polish version of this post I Tamed Wild Devices on Camera! A long, long time ago, in a studio not so far away… I appeared...
Spis treści
×