Conditional Access
Secure Office 365 by requiring compliant devices!
filtruj po kategorii
Filtruj po autorze
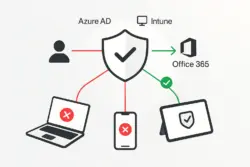
Secure Office 365 by requiring compliant devices!
Opublikowane przez Tomek Sawko

Apple pozamiatało! Migracja MDM, logowanie iPhonem i inne nowości
Opublikowane przez Tomek Sawko

Nowe narzędzia w rękach administratora MDM
Opublikowane przez Tomek Sawko

Czyli Samsung stworzył narzędzie MDM, które mówi płynnie w trzech językach
Opublikowane przez Tomek Sawko

Kompleksowy przewodnik, który zaoszczędzi Ci dziesiątki godzin
Opublikowane przez Tomek Sawko

MDM - o zarządzaniu urządzeniami w organizacji
Opublikowane przez Tomek Sawko

Zabezpiecz Office 365 wymagając zgodnych urządzeń!
Opublikowane przez Tomek Sawko

Dogłębna analiza dla małych, średnich, dużych przedsiębiorstw i sektora publicznego (2024/2025)
Opublikowane przez Tomek Sawko

Jak EMM/MDM wpisuje się w nowoczesną architekturę bezpieczeństwa
Opublikowane przez Tomek Sawko
🇵🇱 Przejdź do polskiej wersji tego wpisu / Go to polish version of this post
Hi! Today we’re tackling a topic that keeps many admins up at night, while simultaneously being one of Microsoft’s most powerful tools for protecting corporate data – Conditional Access in Azure AD, paired with Intune. I’ll show you step by step how to force users (I know, I know, we’re making things difficult for them again 😄) to access your treasures in Office 365 only from devices that meet your corporate security standards. No more logging in from random, unsecured devices! We’ll create a little Fort Knox for your data, but without the need to build a moat and hire dragons.
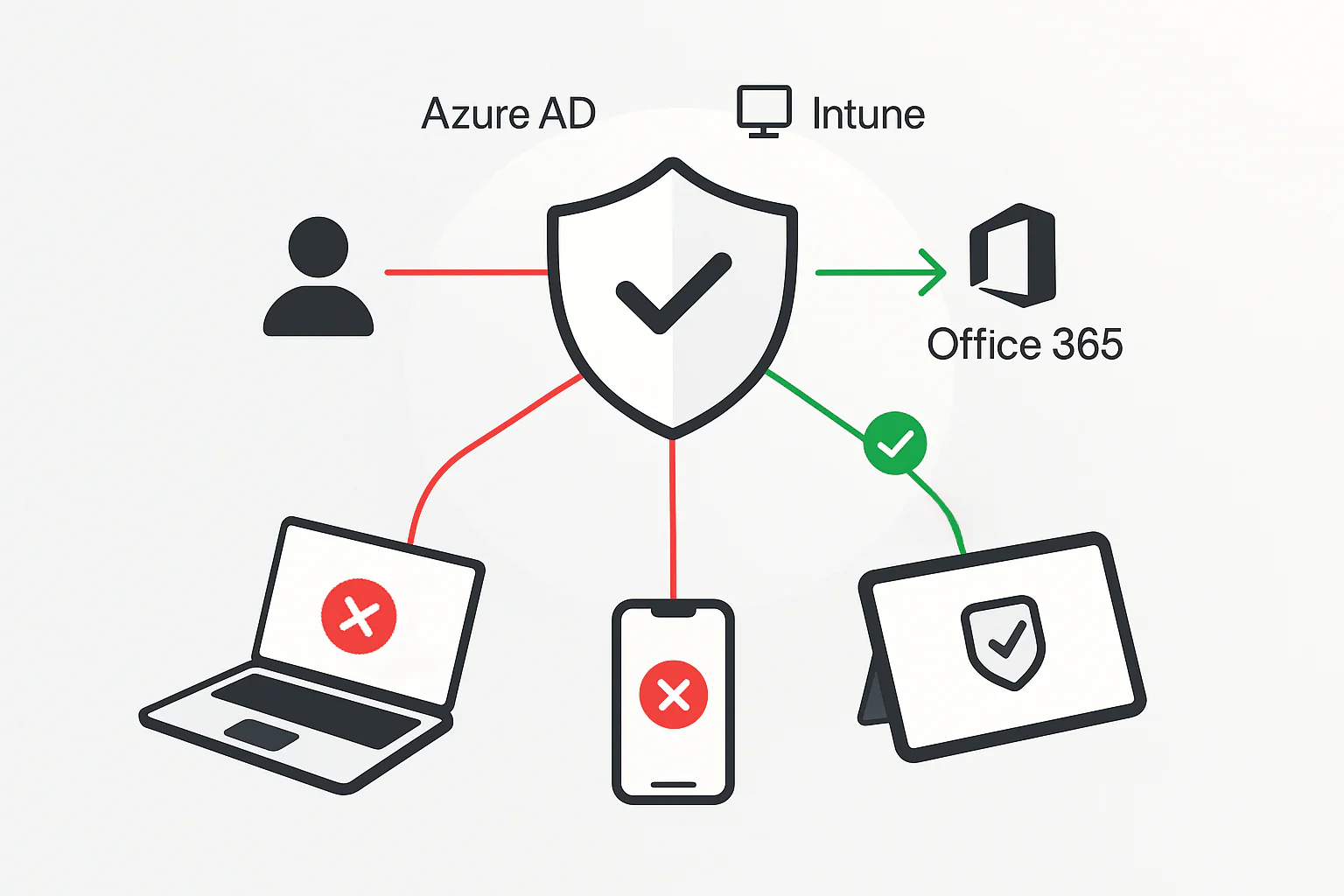
Imagine a bouncer at the entrance to an exclusive club (your corporate data). Conditional Access (CA) is exactly that kind of intelligent bouncer. Before letting someone in (granting access), it checks not only if the person has a ticket (correct login credentials), but also if they meet additional conditions – for example, if they came dressed appropriately (using a trusted device), if they’re sober (the device is secure, compliant with policies), or even checks where they came from (network location).
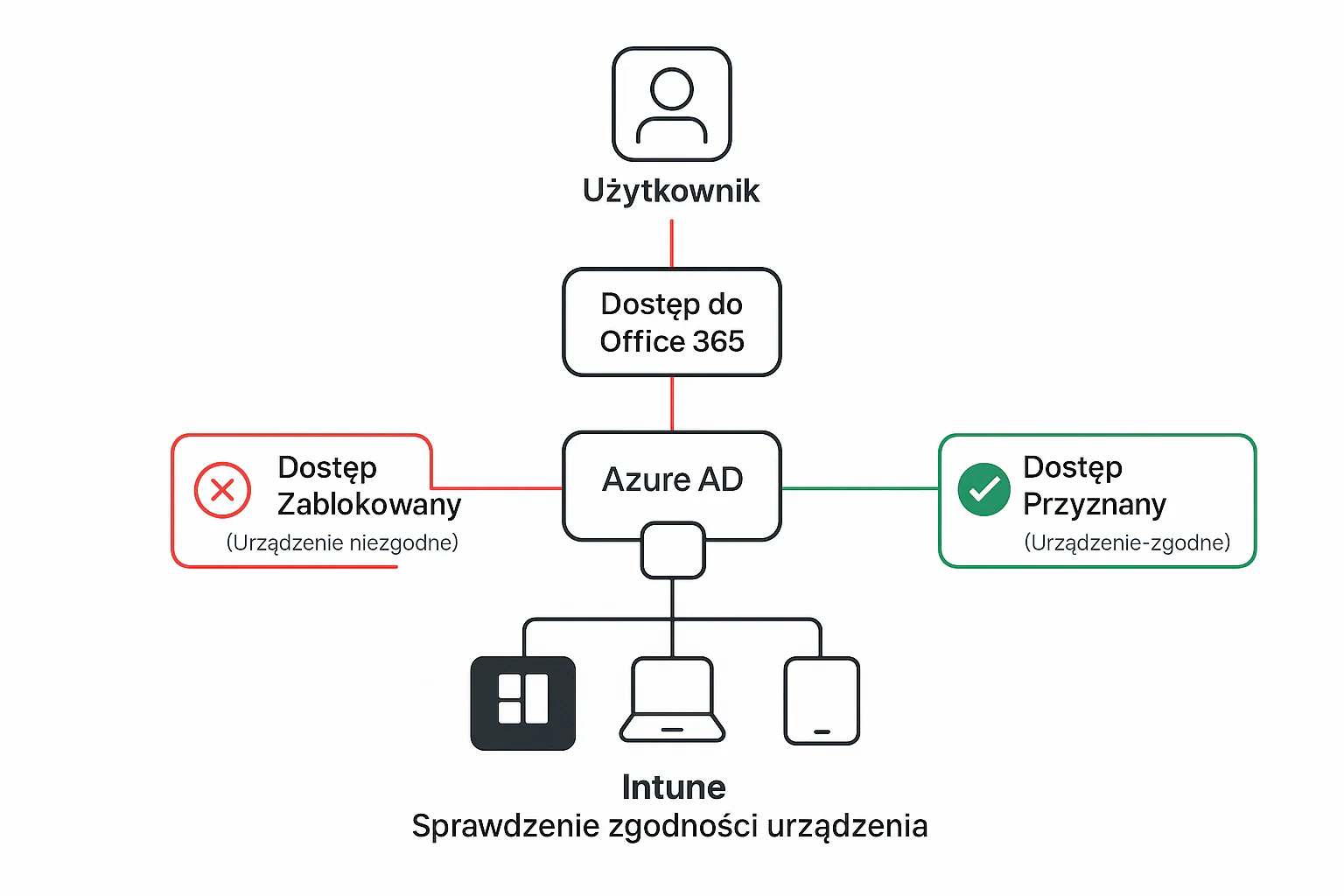
In our case, we’ll combine the forces of Azure AD (which manages identity and login) with Intune (which knows everything about the health status of your devices – whether they’re encrypted, have a PIN, or aren’t „rooted”). Thanks to this, we can create a rule: „Dear user, you want to access Outlook, Teams, or SharePoint (Office 365)? Sure, no problem, but only if you’re connecting from a device that Intune has marked as 'compliant'”. Simple and brilliant, right?
Before we become digital bouncers, let’s make sure we have the right tools:
Got everything? Let’s go!
First, we need to teach Intune how to distinguish a „good” (compliant) device from a „bad” one. We do this using Compliance Policies.
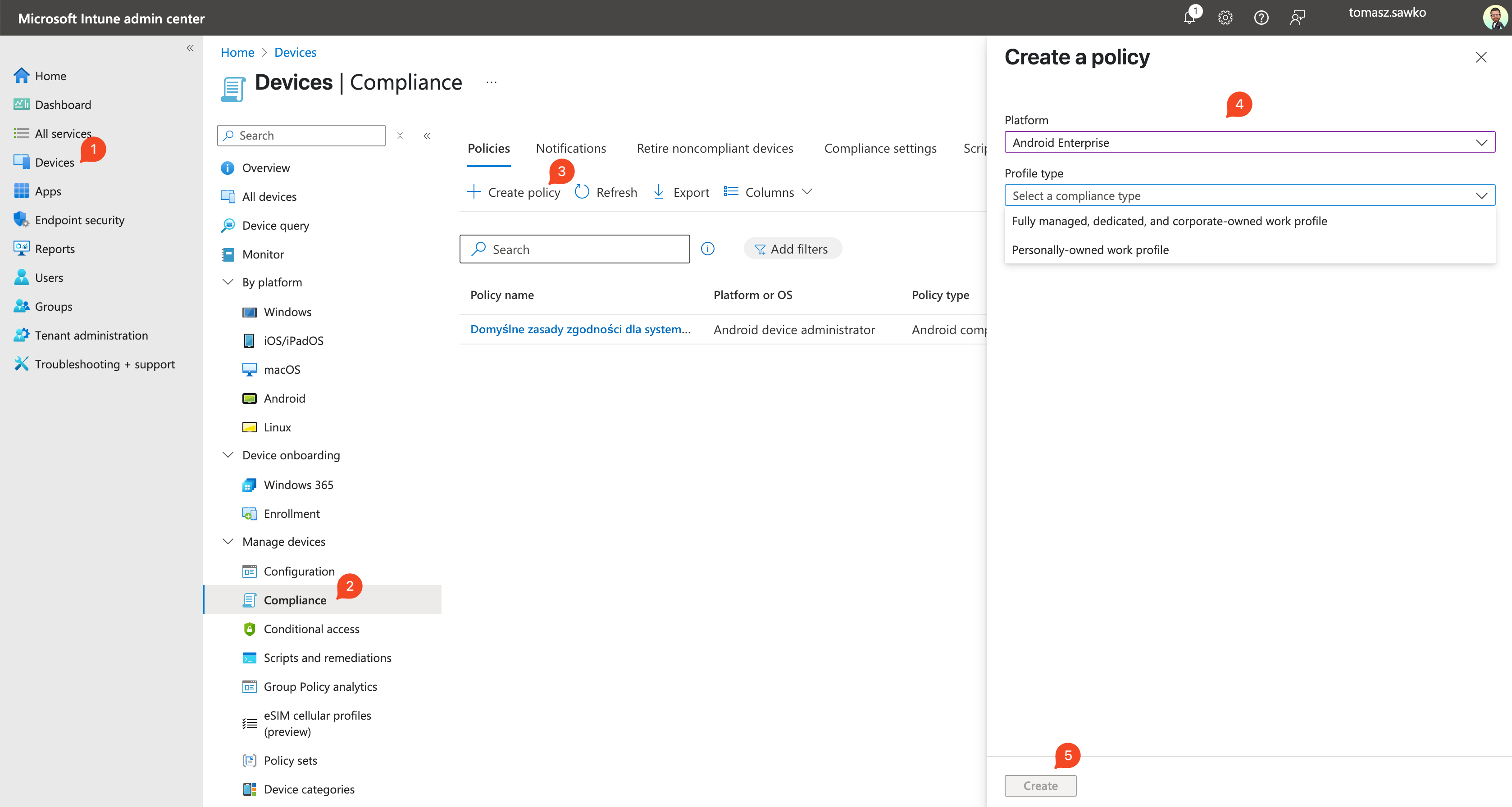
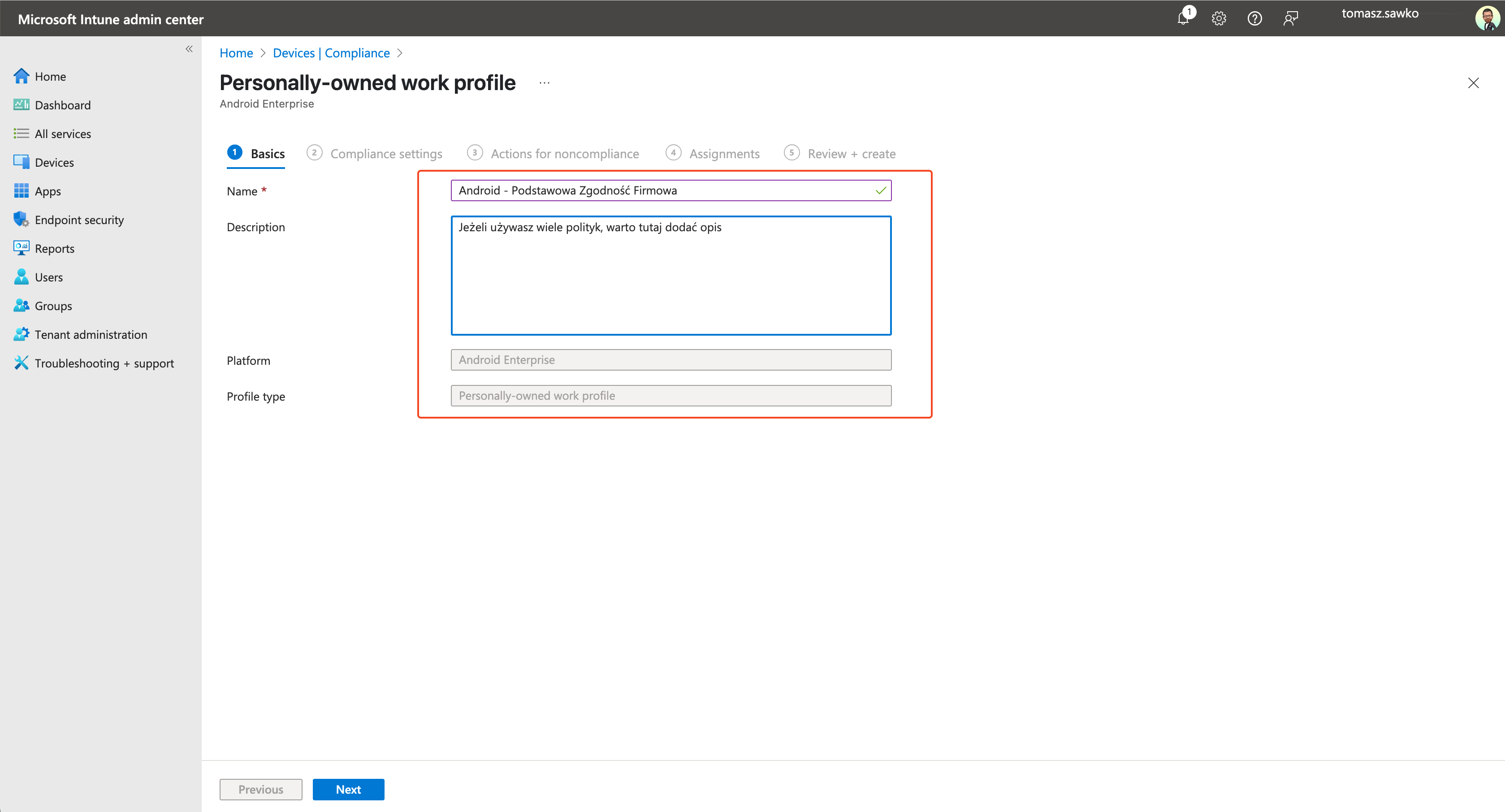
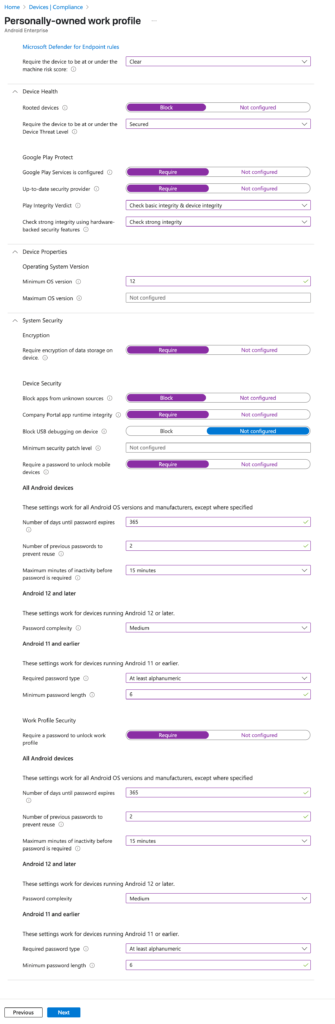
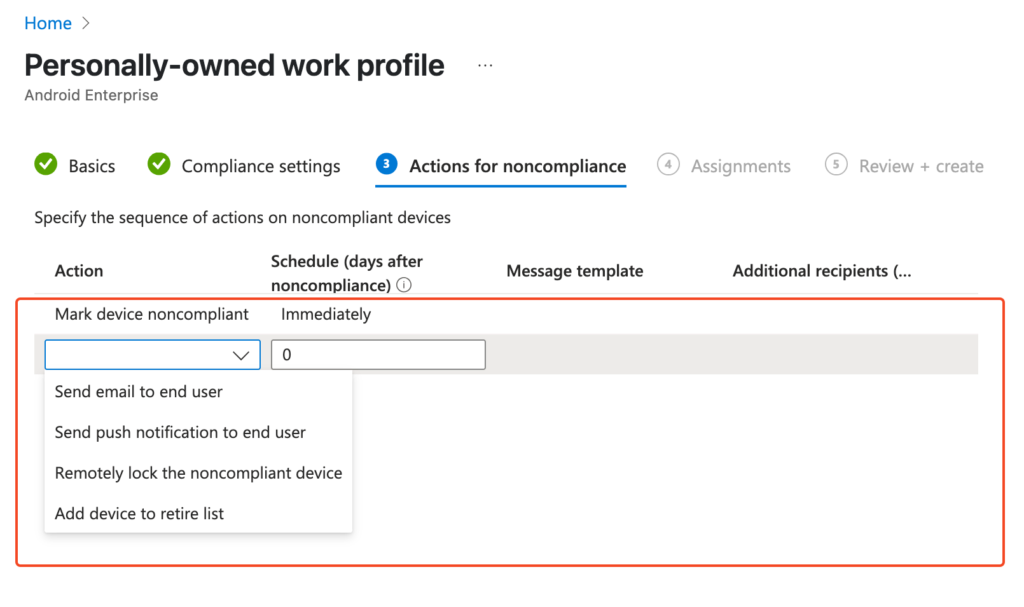
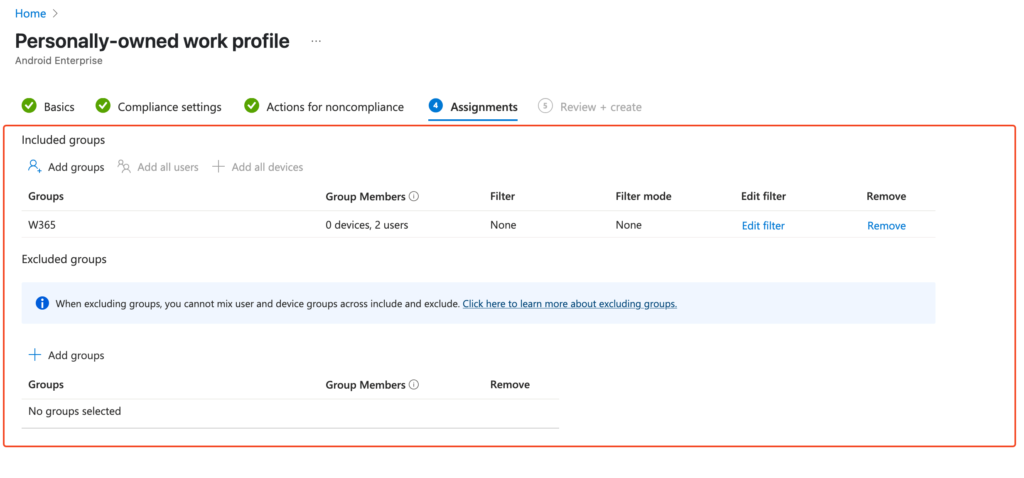
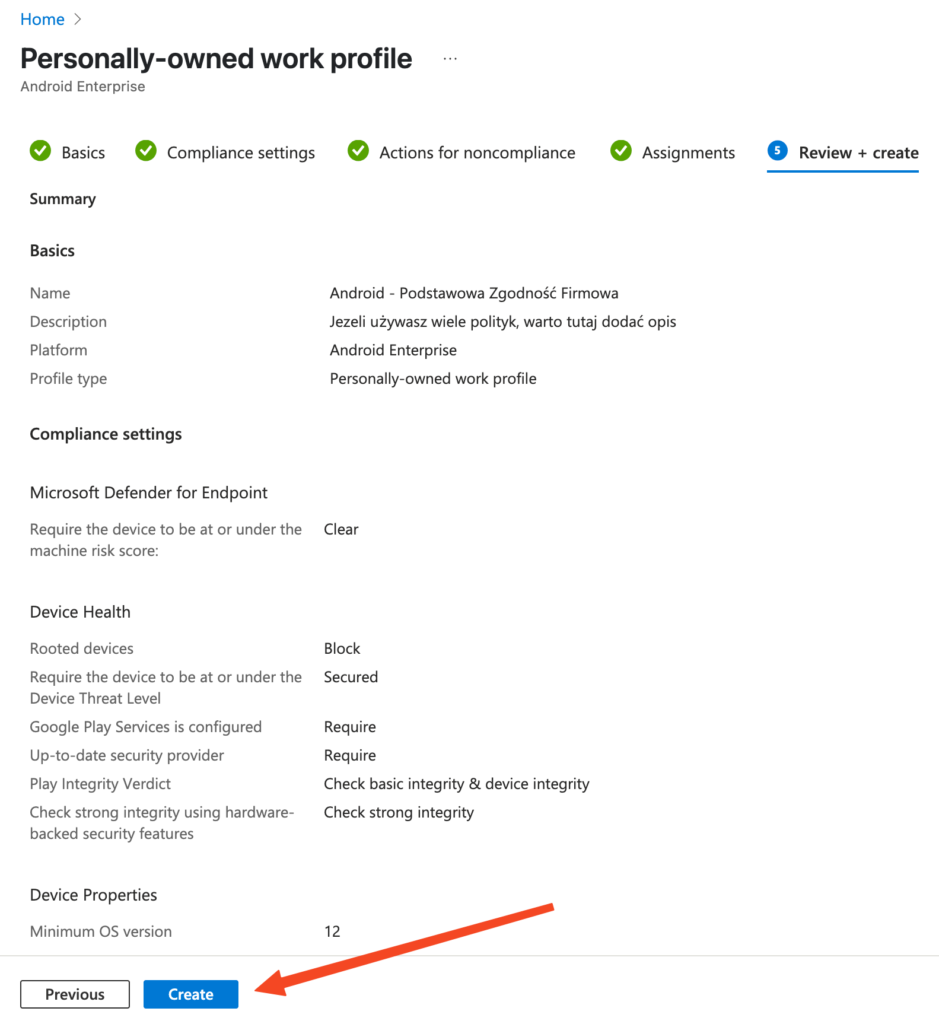
Bravo! You’ve just defined what a „compliant” Android device means in your company. Repeat this process for other platforms (iOS, Windows, macOS) if you manage them.
Now it’s time for our bouncer to work. We’ll configure a Conditional Access policy in Azure AD that will check „tickets” from Intune.
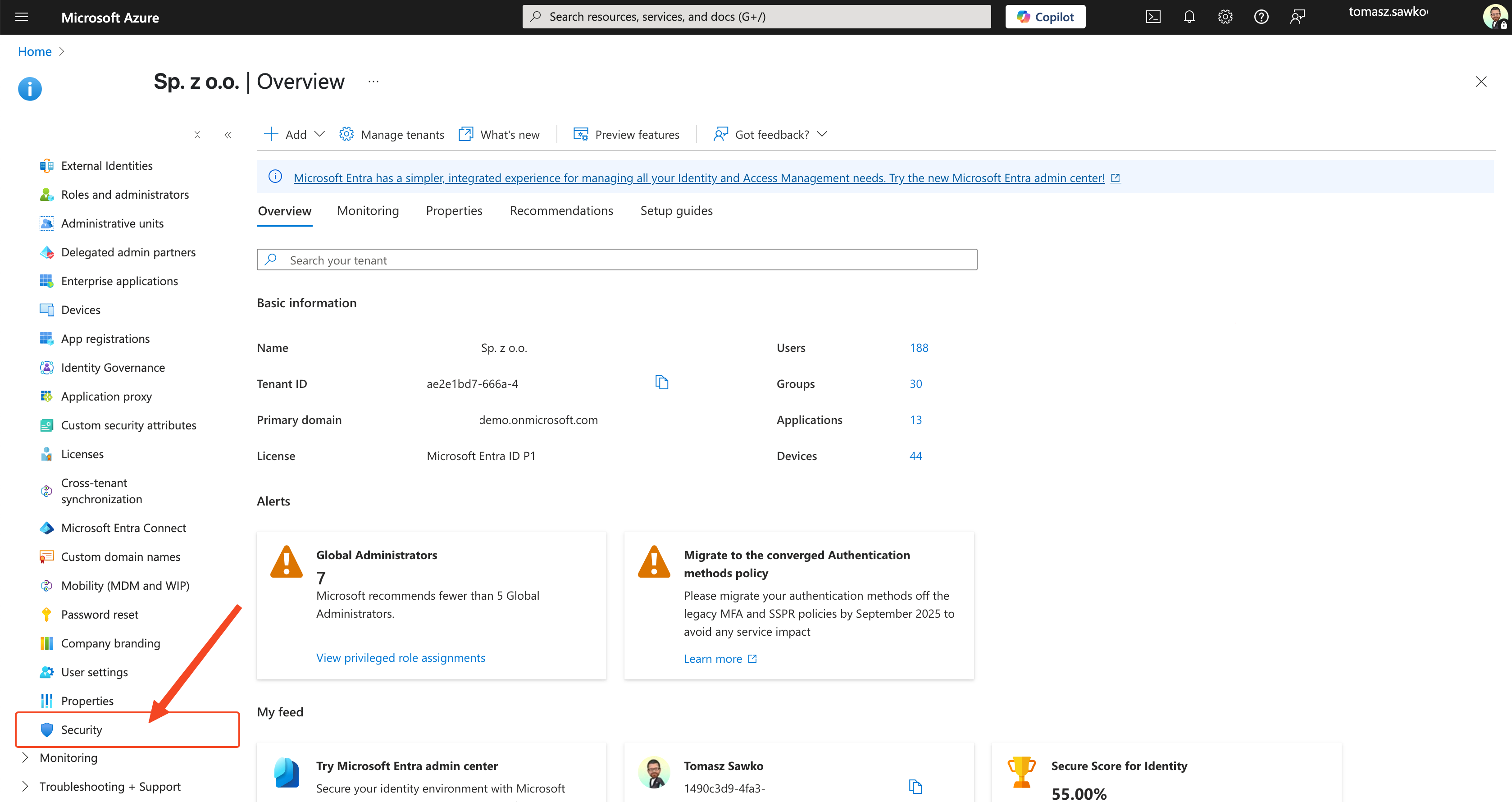
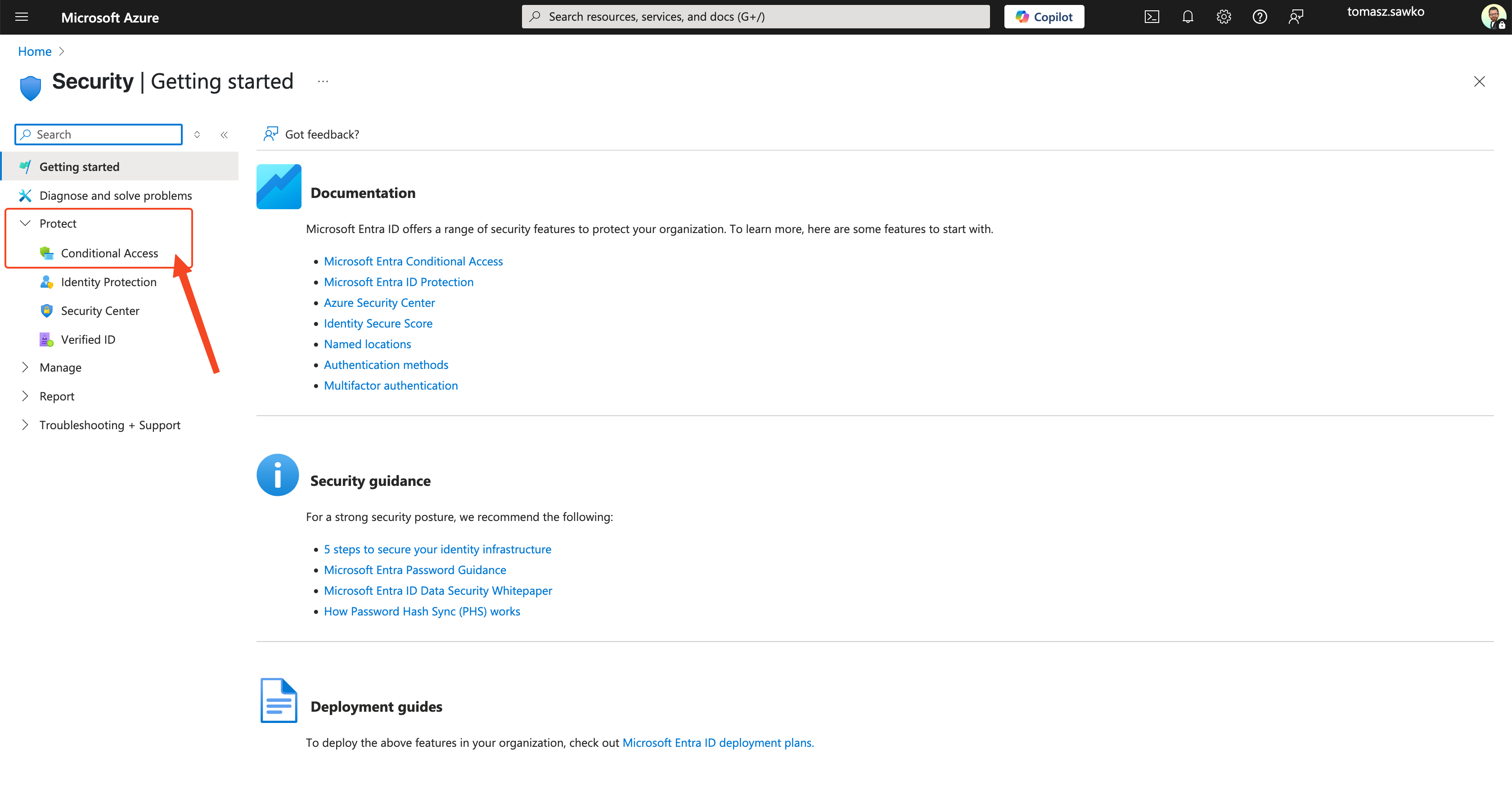
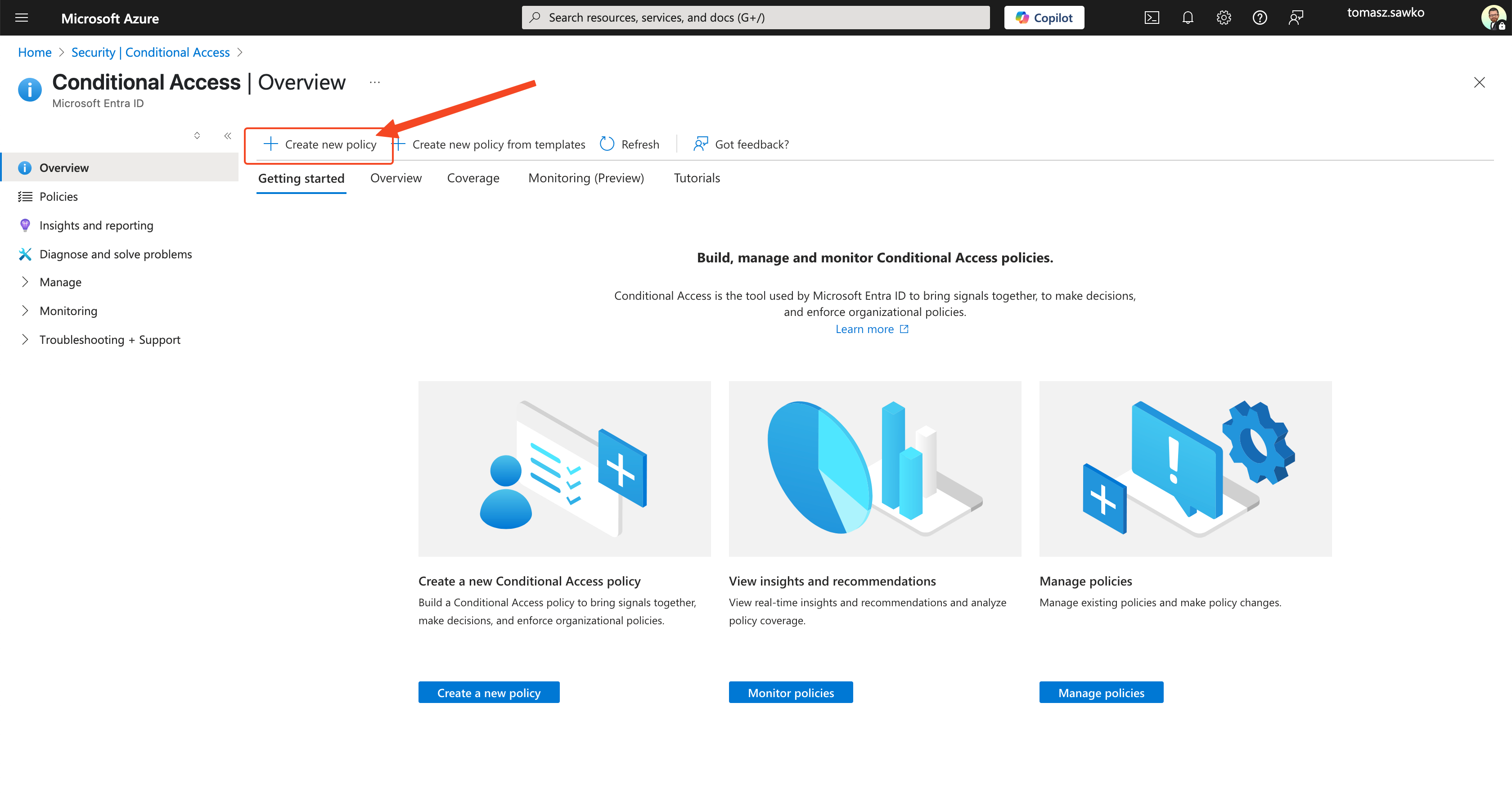
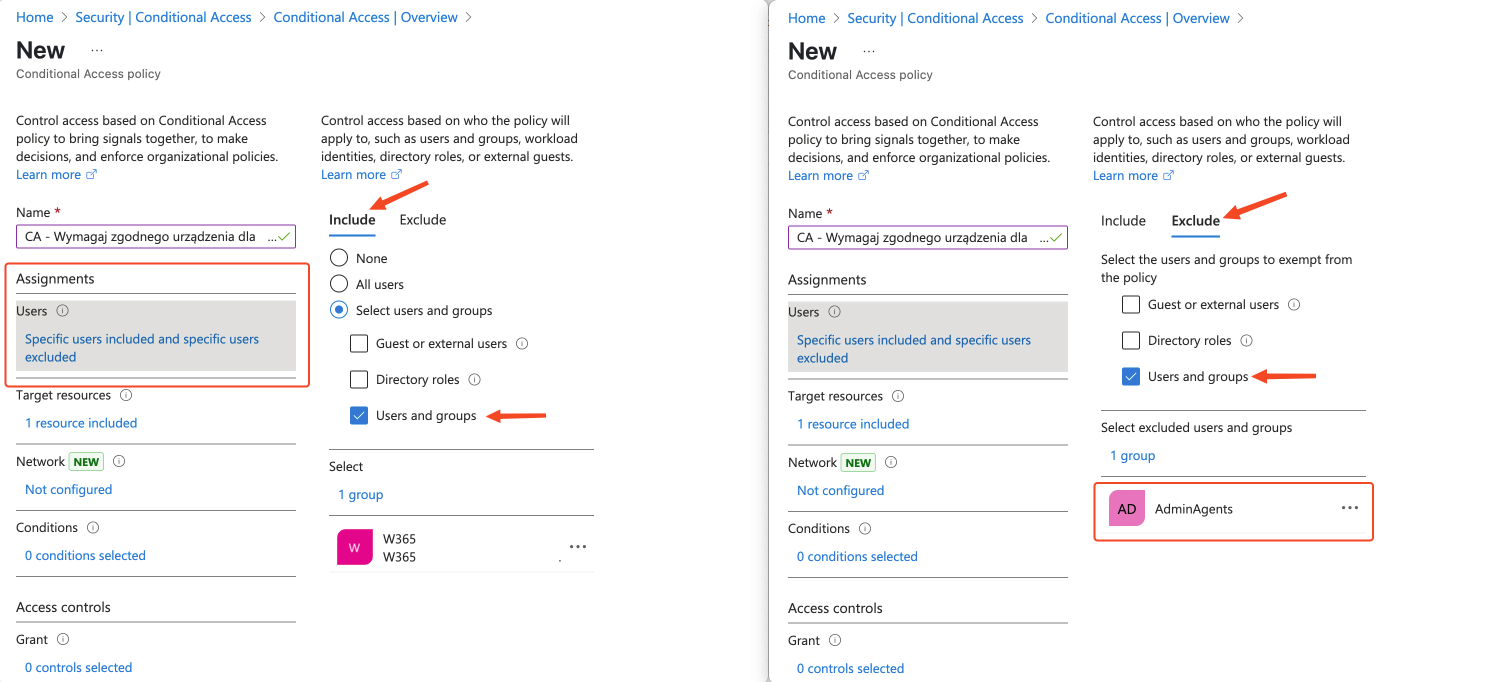
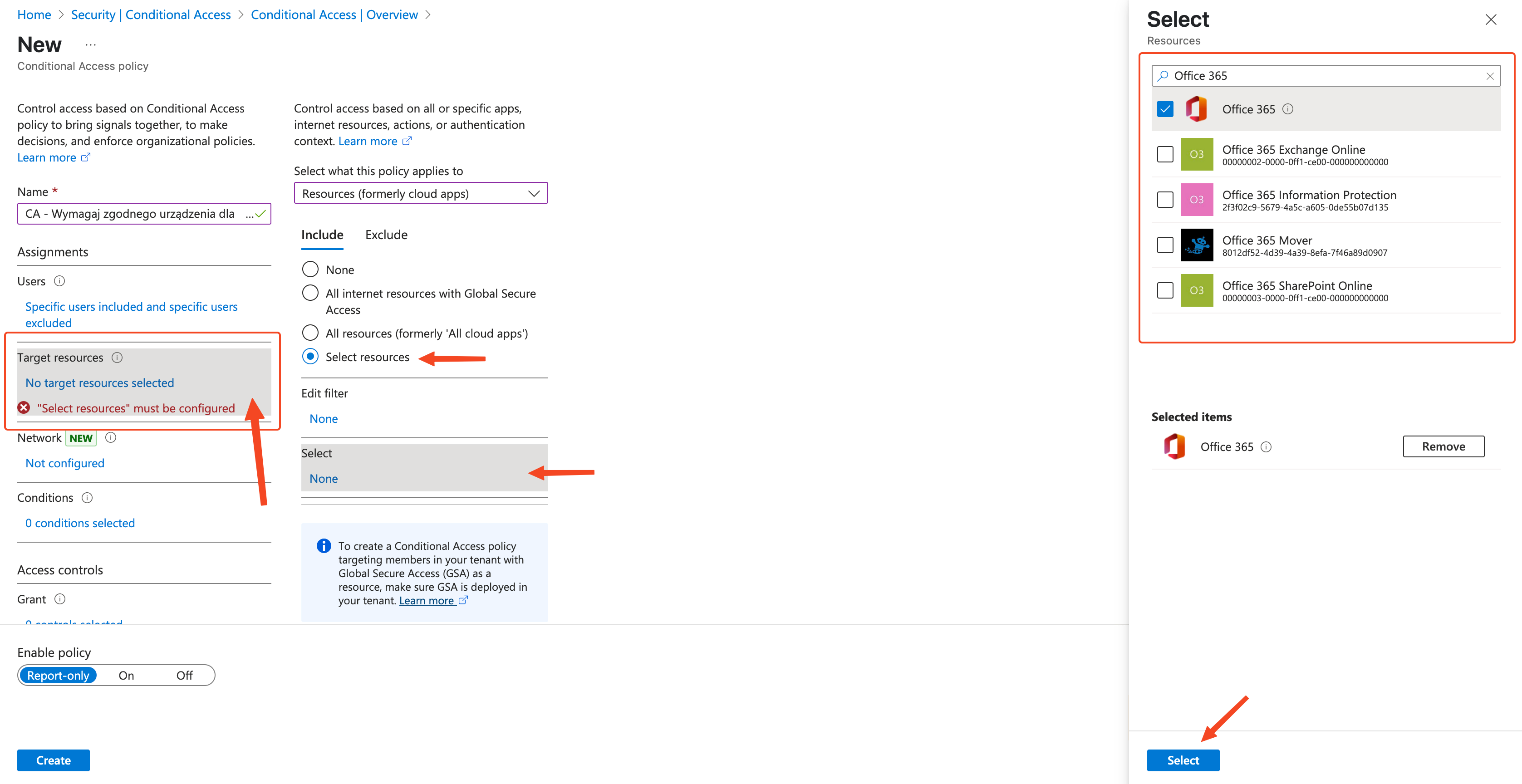

And voilà! Our intelligent bouncer has been configured. Now Azure AD will check with Intune at every attempt to access Office 365 by a user from the assigned group, whether the device they’re connecting from is compliant with the policy we set in Step 1.
Theory is theory, but practice makes perfect (and helps avoid calls from angry users at 7 AM). Time to test our creation:
Remember that synchronization of compliance status between Intune and Azure AD may take a while, so give the system a few to several minutes after making changes or fixing non-compliance on a device.
Congratulations! You’ve just implemented one of the fundamental security measures for accessing data in the Microsoft cloud. Requiring compliant devices through Conditional Access significantly raises the security level, limiting the risk of data leakage from unsecured or compromised devices.
Of course, this is just the beginning. Conditional Access offers much more possibilities – we can add conditions based on location, sign-in risk (requires P2), require MFA, and many others. But this first step – linking device compliance with access – is crucial.
Remember to communicate with users before enabling the policy in „On” mode. Explain to them why you’re doing this and what they need to do to make their devices compliant. A bit of prevention will save you a lot of helpdesk work later. 😊
Good luck with implementation.
Until next time!
Cześć! Dziś na warsztat bierzemy temat, który spędza sen z powiek wielu adminom, a jednocześnie jest jednym z najpotężniejszych narzędzi w arsenale Microsoftu do ochrony firmowych...

Tradycyjne podejście do bezpieczeństwa IT staje się coraz mniej skuteczne w dobie pracy zdalnej, chmury obliczeniowej i wszechobecnych urządzeń mobilnych. W odpowiedzi na te...