Android Zero Touch with Microsoft Intune
A comprehensive guide that will save you dozens of hours
filtruj po kategorii
Filtruj po autorze

A comprehensive guide that will save you dozens of hours
Opublikowane przez Tomek Sawko

How EMM/MDM fits into modern security architecture
Opublikowane przez Tomek Sawko

So Samsung has created an MDM tool that speaks three languages fluently
Opublikowane przez Tomek Sawko

Apple has swept the board! MDM migration, iPhone login, and other new features
Opublikowane przez Tomek Sawko

New tools in the hands of the MDM administrator
Opublikowane przez Tomek Sawko
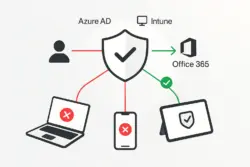
Secure Office 365 by requiring compliant devices!
Opublikowane przez Tomek Sawko

Apple pozamiatało! Migracja MDM, logowanie iPhonem i inne nowości
Opublikowane przez Tomek Sawko

Nowe narzędzia w rękach administratora MDM
Opublikowane przez Tomek Sawko

Czyli Samsung stworzył narzędzie MDM, które mówi płynnie w trzech językach
Opublikowane przez Tomek Sawko

Kompleksowy przewodnik, który zaoszczędzi Ci dziesiątki godzin
Opublikowane przez Tomek Sawko

A comprehensive guide that will save you dozens of hours
🇵🇱 Przejdź do polskiej wersji tego wpisu / Go to polish version of this post
Sit back comfortably, because I’m taking you on a journey to a world where corporate Android smartphones configure themselves practically on their own. Today we’re taking on one of the favorite duets: Android Zero Touch and Microsoft Intune. I’ll show you how to combine these two powerful forces so that deploying new devices in your company is faster than your morning coffee.
No more manually clicking through dozens of screens on each new phone. No more asking users to „install something from the store”. We do it once, and we do it right. Automagically!
Imagine the ideal scenario: a courier brings a package with brand new smartphones to your company. You hand the box to an employee. They open it, turn on the phone, connect to Wi-Fi and… magic happens. The device knows on its own that it belongs to your company, downloads the appropriate configuration, installs business applications, sets passwords, Wi-Fi and whatever you wish. The user only needs to enter their login credentials and after a few minutes they have a fully ready, secure and managed work tool. That’s exactly what Android Zero Touch (AZT) is.
But awareness of belonging alone isn’t everything. The device still needs to know what to do. And here he enters the stage, all in white (or rather in blue) – Microsoft Intune, which will be the brain of the entire operation.
Before we start, make sure you have everything at hand. From experience, I know that missing one element can stop the entire process for long hours.
Not every Android phone is suitable for this game. You need to have devices that:
My advice: Before placing an order, ask your supplier directly (e.g., in the business service department of Plus, Orange or T-Mobile) whether the selected models are compatible with Zero Touch and whether they can register them for you.
md*******@*********ny.com, and be sure to secure it with two-factor authentication (2FA).1. Go to: https://accounts.google.com/signupwithoutgmail
2. Use a corporate email address like: md*******@*********ny.com
3. Be sure to enable two-step verification – seriously, I’m not kidding
And here we come to the key issue. You can’t „click through” the portal yourself. It must be created for you by an authorized reseller / Google partner.
How to get an account in the Zero Touch portal? (short instructions for the impatient):
Before devices start reporting, we need to prepare a place for them in Intune.
This is the absolute foundation. If you already have this, skip to step 2.
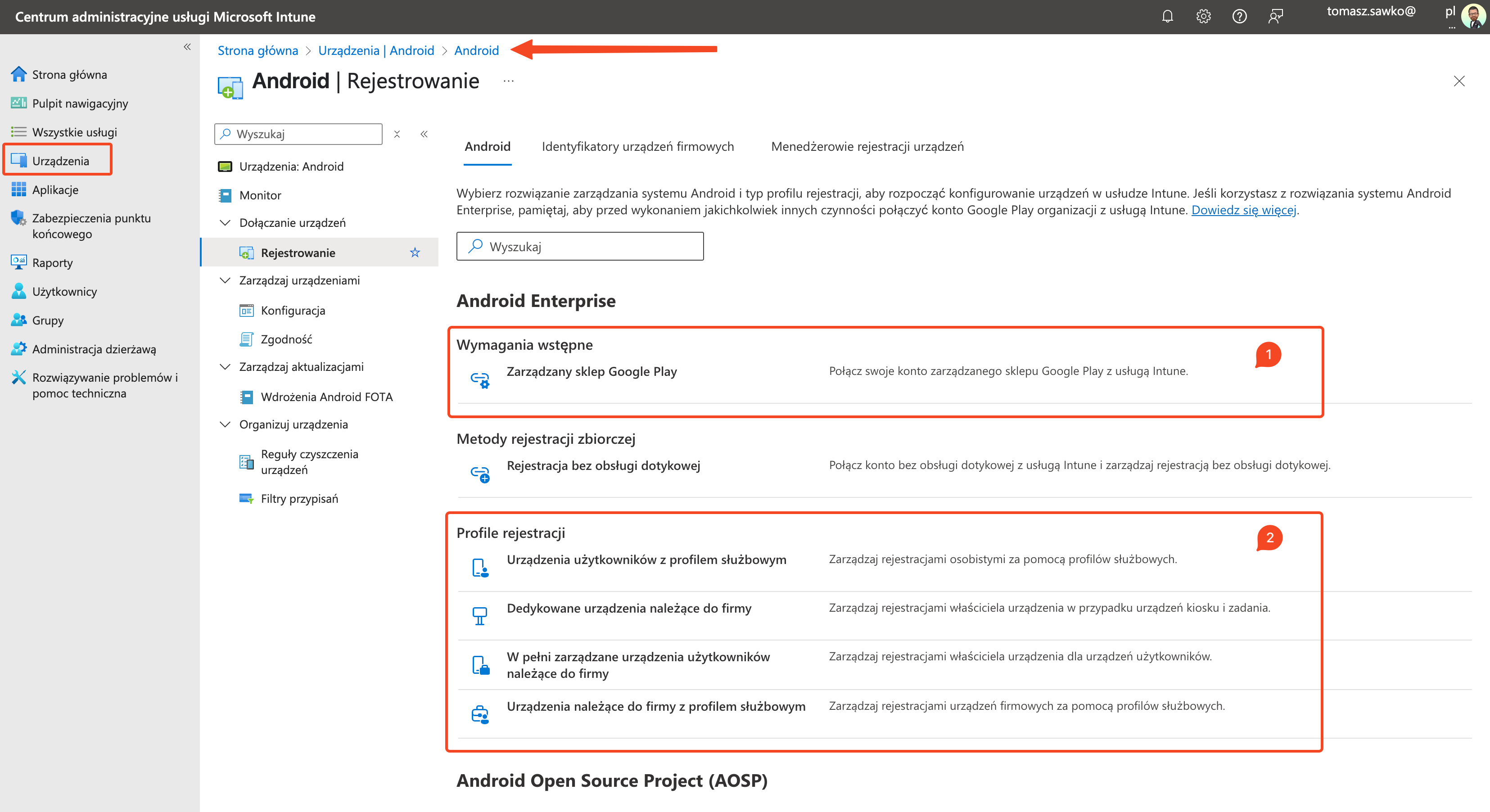
Now we’ll create a profile that will generate a „magic spell” for us – a token.
AZT - Default Profile.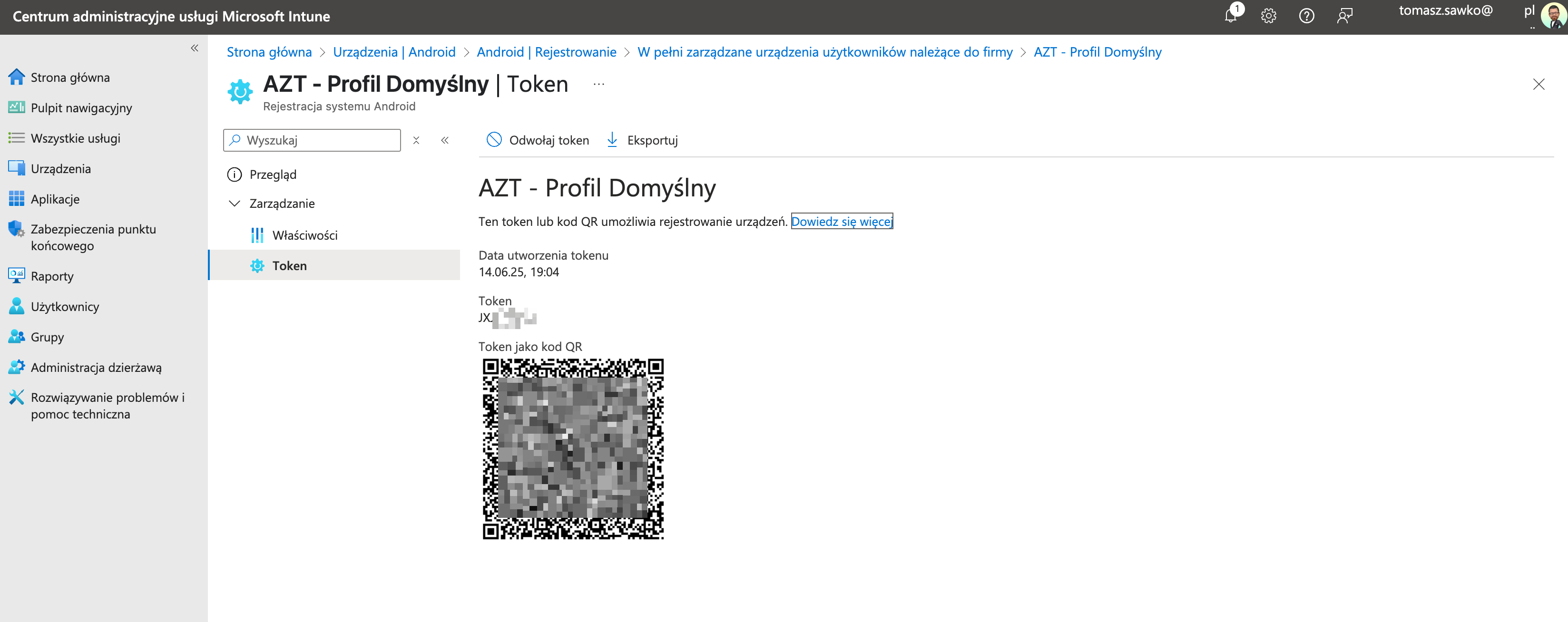
Now it’s time for magic in the AZT portal. You have two options.
Intune offers a built-in, simplified tool for connecting with AZT. Ideal if you have one standard configuration for everyone.
Disadvantage: This method allows you to create only one default configuration. If you need different settings for different departments (e.g., salespeople with CRM, warehouse workers with a scanning app), you need to choose method #2.
This is where the real, granular fun begins.
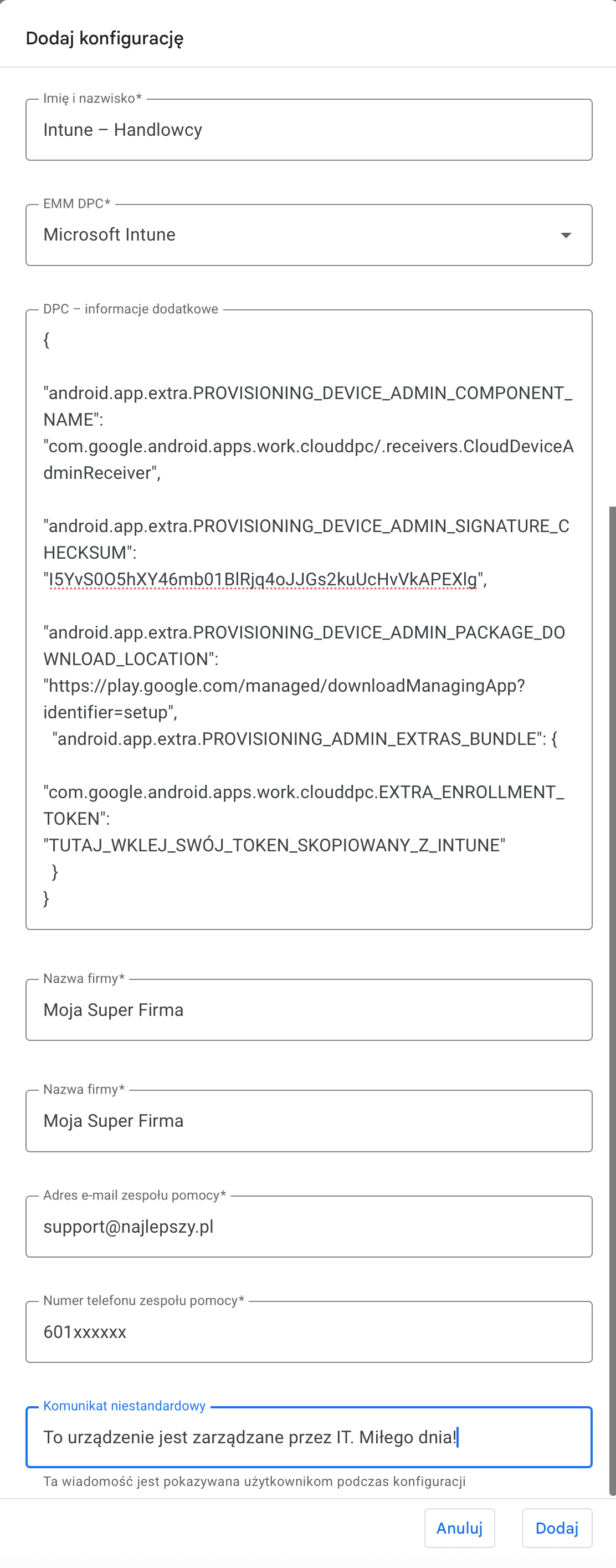
Here’s the complete JSON template you should use:
{
"android.app.extra.PROVISIONING_DEVICE_ADMIN_COMPONENT_NAME": "com.google.android.apps.work.clouddpc/.receivers.CloudDeviceAdminReceiver",
"android.app.extra.PROVISIONING_DEVICE_ADMIN_SIGNATURE_CHECKSUM": "I5YvS0O5hXY46mb01BlRjq4oJJGs2kuUcHvVkAPEXlg",
"android.app.extra.PROVISIONING_DEVICE_ADMIN_PACKAGE_DOWNLOAD_LOCATION": "https://play.google.com/managed/downloadManagingApp?identifier=setup",
"android.app.extra.PROVISIONING_ADMIN_EXTRAS_BUNDLE": {
"com.google.android.apps.work.clouddpc.EXTRA_ENROLLMENT_TOKEN": "PASTE_YOUR_TOKEN_COPIED_FROM_INTUNE_HERE"
}
}What do these mysterious lines mean? Let me explain:
PROVISIONING_DEVICE_ADMIN_COMPONENT_NAME: points to a specific application component (in this case the Google agent) that will manage the devicePROVISIONING_DEVICE_ADMIN_SIGNATURE_CHECKSUM: this is the checksum of the agent application certificate, guarantees that the phone downloads the correct and secure application, not some impersonating malwarePROVISIONING_DEVICE_ADMIN_PACKAGE_DOWNLOAD_LOCATION: the URL from which the agent should be downloadedEXTRA_ENROLLMENT_TOKEN: this is exactly your unique token from Intune, which tells the agent: „report to THIS specific organization in THIS specific MDM service”Pro-tip for advanced users: You can expand the PROVISIONING_ADMIN_EXTRAS_BUNDLE section with additional parameters to automate the process even more:
"android.app.extra.PROVISIONING_LOCALE": "pl_PL" – sets the default Polish language"android.app.extra.PROVISIONING_TIME_ZONE": "Europe/Warsaw" – sets our time zone"android.app.extra.PROVISIONING_LEAVE_ALL_SYSTEM_APPS_ENABLED": false – causes most manufacturer-preinstalled applications (so-called bloatware) to be hidden, leaving only the essential onesAfter completing the JSON, save the configuration. Now in the Devices tab you can assign it as default or select specific devices and assign them this profile.
When the user turns on a new phone and connects it to the internet, the process should start automatically.

Android Zero Touch integrated with Microsoft Intune is no longer a futuristic vision, but a powerful tool available here and now. The initial configuration, as you can see, requires focus and attention to detail, but it’s a one-time effort. The reward is huge time savings, iron-clad fleet standardization and peace of mind, because every device is secure from the first boot.
If you’re thinking about this seriously, start with a conversation with the operator. Ask, negotiate, use their knowledge. And then enjoy the sight of phones that configure themselves. It’s one of those feelings in an admin’s work that makes life worth living!
And once everything is working as it should, get interested in the topic of Conditional Access 😉
Until next time!
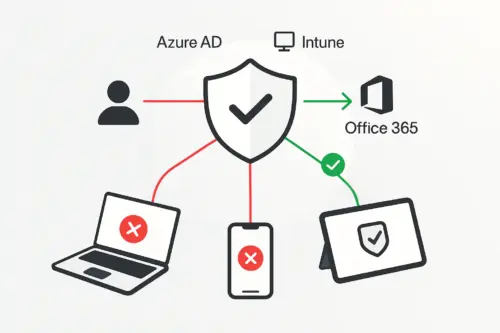
Cześć! Dziś na warsztat bierzemy temat, który spędza sen z powiek wielu adminom, a jednocześnie jest jednym z najpotężniejszych narzędzi w arsenale Microsoftu do ochrony firmowych...

Polski rynek rozwiązań do zarządzania mobilnością przedsiębiorstw (Enterprise Mobility Management - EMM) i zarządzania urządzeniami mobilnymi (Mobile Device Management - MDM)...